It’s been a minute since I’ve posted on my blog but I’ve had an exciting year talking to customer about the Microsoft Defender story, which in 2021 has been named a Gartner Magic Quadrant leader in the Endpoint Protection space. As it brings the traditional antimalware service execuable MsMpEng.exe, introduces the SenseCE.exe engine, and more that I covered in my MMS session about Defender, protecting the endpoint beyond real time protection sits at the core of Windows 10 by way of Attack Surface Reduction.
Contents
Why Attack Surface Reduction?
behaviors are often considered risky because they are commonly abused by attackers through malware. Attack surface reduction rules can constrain software-based risky behaviors – and Microsoft has a full list of attack surface reduction rules documented – protecting you from Office, Adobe, Javascript, and more exploits.
So How’s It Licensed?
There is no license: its built into Windows, however there is a note from Microsoft around LMAR (logging, monitoring & reporting)
Although attack surface reduction rules don’t require a Windows E5 license, if you have Windows E5, you get advanced management capabilities. The advanced capabilities – available only in Windows E5 – include:
- The monitoring, analytics, and workflows available in Defender for Endpoint
- The reporting and configuration capabilities in Microsoft 365 Defender.
Now that we’ve covered the Concepts, let’s talk about the options for deployment
Option E[asy] = Intune:
-
- Deploy policies and target machines
- Guidance: Working with Attack Surface Reduction rules to reduce the attack surface of applications – All about Microsoft Endpoint Manager (petervanderwoude.nl)
Option [S]CCM = Configuration Manager
-
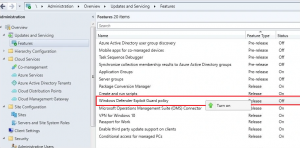
- Enable Windows Defender Exploit Guard in SCCM
- Configure Exploit Guard policy in SCCM and deploy to your Device collection
- Guidance: Deploy Windows Defender Exploit Guard Using SCCM (pelegit.co.il)
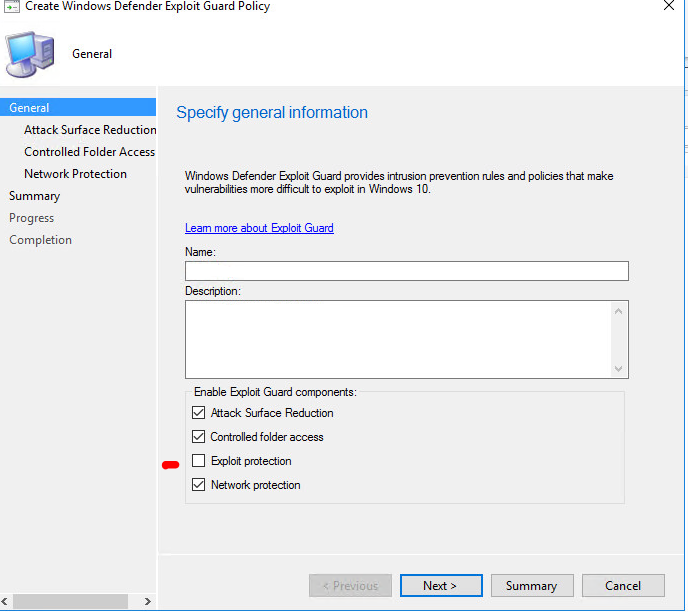
- Select all policies except off on “Exploit Protection” for a moment. (EG requires an XML file which must be custom crafted
- Configure ALL Attack Surface Reduction Rules (Either Block or Enabled) except Controlled folder access
- Set Controlled Folder access to Audit
- Understand attack surface rules
- Set Controlled Folder access to Audit
- Set Network Protection to Block
Testing & Logging
Want to know the effectiveness? Visit the Attack Surface Reduction – Microsoft Defender Testground to download the Microsoft tool to evaluate
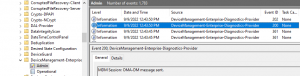
To Review WHICH rules are firing off is not the easiest process if you DONT have an E5 license, but Microsoft has provided steps to ingest the XML log into Event Viewer for better consumption.