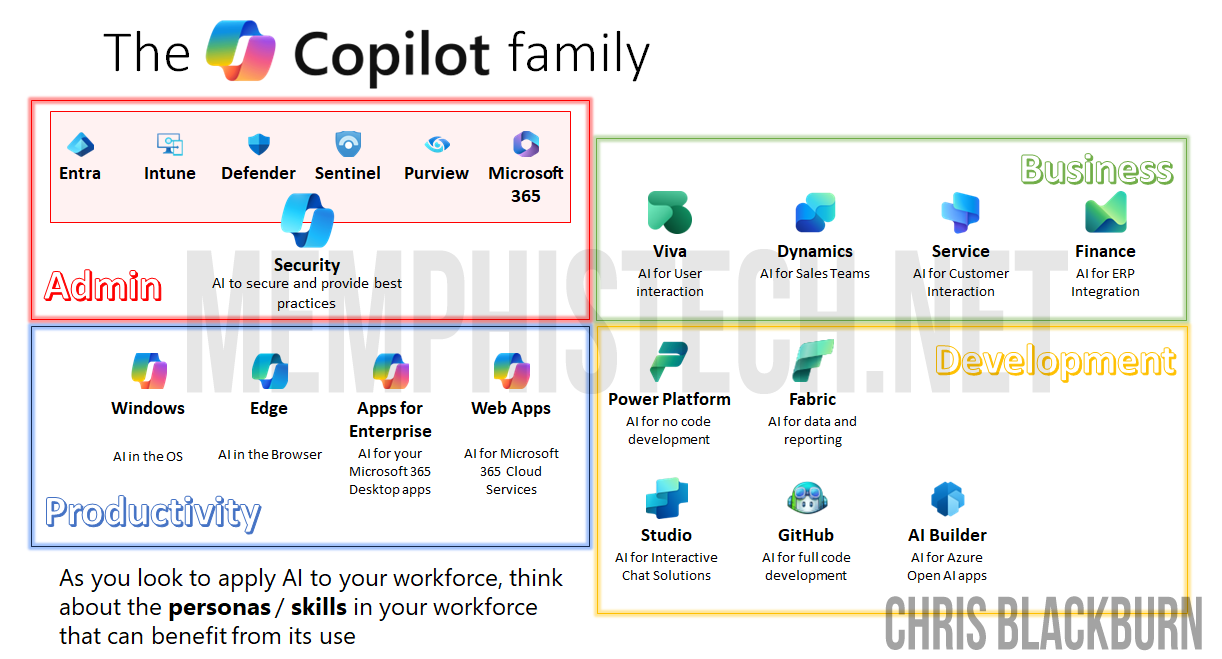
Synopsis • As AI becomes deeply integrated into workplace productivity, understanding and governing its usage is critical for IT leaders. • Learn how to explore native Microsoft 365 capabilities to monitor, analyze, and secure...
Read More
Modernizing User Lifecycles with Microsoft Entra
The Minnesota Microsoft 365 User Group held their 14th biannual workshop day, and once again I was grateful for the opportunity to present, sharing my insights and experiences on modernizing identity governance using Microsoft...
Read More
4 Minutes
OneDrive is causing your Powershell PAIN!
After many hours of research and troubleshooting, I found that OneDrive was the culprit of my Powershell pain. This is all in part to Microsoft’s default of putting modules (that are installed under the...
Read More
3 Minutes
Improving human communication by leveraging the RIGHT Copilot
From the dawn of computing, one story remains: our data is the same, but the way it’s presented has changed. we’re always striving to improve efficiency with how we work and how we communicate....
Read More
1 Minute
Considerations enabling Microsoft 365 Copilot!
Excited to have #Microsoft365 #Copilot licensed and enabled in my personal tenant! For those diving in for the first time here are a few observations of note that I shared in the Concurrency, Inc....
Read More
3 Minutes
Minnesota M365 User Group 11th bi-annual Fall 2023 In-Person Workshop Day Conference
It was a delight to be back speaking for our amazing Minnesota Microsoft community as part of the M365 Fall Workshop Day 2023 – MN Microsoft 365 User Group (mn365.org) 2 sessions. 6 hours....
Read More
5 Minutes
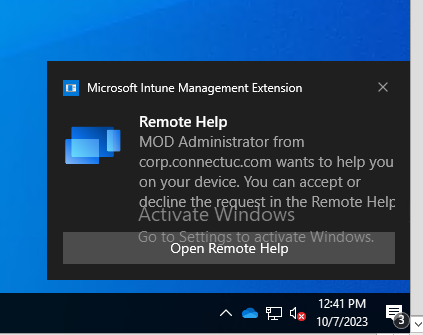
Quickly Enable Windows Devices for Intune Remote Help
Use Powershell scripting to easily deploy Remote Help for leveraging Intune for Remote Assistance...
Read More
9 Minutes
Getting Copilot in Windows 10/11
Intro Updated on 4/3/2024: includes Windows 10 steps & removes Insider Program requirement for Windows 11 With the ability to kickstart your AI-powered experience. Copilot in Windows bring you exciting capabilities to enhance your...
Read More
10 Minutes
Effortlessly Conquor Common Microsoft MDM Enrollment Errors
It’s been a while since I’ve blogged here but it’s certainly not for lack of content, but rather for lack of time! I’ve been working on tons of modern endpoint projects transitioning clients to...
Read More
3 Minutes
Its not JUST about Defender: Attack Surface Reduction Practices
It’s been a minute since I’ve posted on my blog but I’ve had an exciting year talking to customer about the Microsoft Defender story, which in 2021 has been named a Gartner Magic Quadrant...
Read More