Microsoft recently released a very helpful script that allows Administrators looking to roll out Azure MFA to their organization with a easy-to-read output that can aid in assessing status, or even recommendations to enhance their use of the technology.
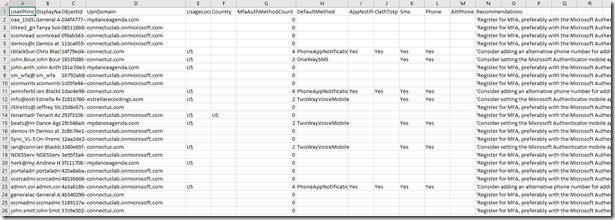
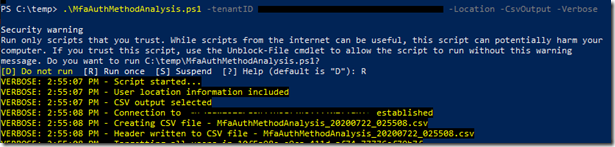
Below is a sample output:
Here are some common “Recommendations” from the script
- ‘Register for MFA, preferably with the Microsoft Authenticator mobile app and also with a phone number, used for SMS or Voice.’
- ‘Consider adding an alternative phone number for additional resilience.’
- ‘Consider setting the Microsoft Authenticator mobile app as the default method.’
- ‘Register at least another authentication method, preferably the Microsoft Authenticator mobile app or hardware OATH token. A user can have up to five hardware OATH tokens or mobile apps registered.’
- ‘Consider adding an alternative phone number for additional resilience.’
Implementation
Download the ZIP file from the Microsoft website.
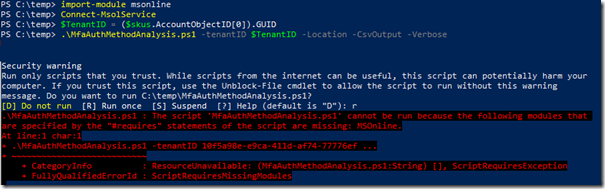
Run the following Powershell commands to Authenticate to your tenant and run the commands
Import-Module MSONLINE
Connect-MSOLService
$TenantID = ($skus.AccountObjectID[0]).GUID
.\MfaAuthMethodAnalysis.ps1 –tenantID $TenantID -Location -CsvOutput –Verbose
You’ll may see the following error:
If this occurs, you will need the MSONLINE module, and may need to update as I had to do by running the following Powershell command:
Update-Module MSONLINE
Once updated, try running the command again and you should see the process fire off and save a file in the directory of the script in the format MfaAuthMethodAnalysis_<date>_<time>.csv
This is WAY easier than using the GUI in Azure Active Directory, and allows you to do some sort again the data for taking action, automation, etc.